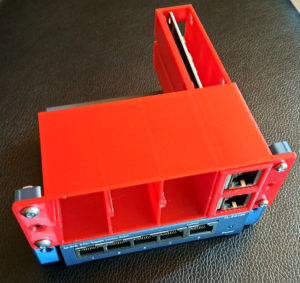
Klinge is an FPGA-based blade server suitable for building trusted networks. Klinge is especially suitable for this because its SOC/CPU is completely auditable and can be built and updated using 100% open-source software.
This post is a quick guide for setting up a private trusted network using two Klinge servers and a 5-port switch. This guide assumes you’re using Kakao Linux. Check out our Half10 repo for a 3D-printable rack system.
The network will look like this:
[ Internet ] | [ Router / LAN (untrusted) ] | [ Klinge #1 - DMZ (semi-trusted) ] | [ Klinge #2 - Perimeter (trusted) ] | [ 5-port switch - Trusted LAN ]
In this setup the perimeter can act as a firewall limiting or completely excluding traffic from the DMZ to the trusted network.
Here are the benefits of this setup according to ChatGPT:
| Feature | One Server | Two Servers |
|---|---|---|
| Security Zones | Single, flat | Clearly separated (DMZ vs LAN) |
| Defense-in-Depth | No | Yes |
| Exposure Management | High | Minimized |
| Compromise Containment | Poor | Better (breach isolation) |
| Policy Granularity | Limited | Fine-grained control |
| Service Isolation | Minimal | Strong |
Configuration
Connecting the Ethernet cables is straightforward. The eth0 port on Klinge #1 connects to your existing LAN and the eth1 port connects to the eth0 port of Klinge #2. The eth1 port of Klinge #2 connects to the 5-port switch, which is the trusted network.
Configuring Klinge #1 (DMZ):
# enable ip forwarding $ cat net.ipv4.ip_forward=1 >> /etc/sysctl.conf $ sysctl -p # edit /etc/network/interfaces: auto eth0 iface eth0 inet dhcp auto eth1 iface eth1 inet static address 10.10.10.1 netmask 255.255.255.0
Configuring Klinge #2 (Perimeter):
# edit /etc/network/interfaces: auto eth0 iface eth0 inet static address 10.10.10.2 netmask 255.255.255.0 auto eth1 iface eth1 inet static address 10.20.0.1 netmask 255.255.0.0 # to configure DHCP on the trusted LAN, edit /etc/dnsmasq.conf: interface=eth1 dhcp-range=10.20.0.100,10.20.0.199,12h dhcp-option=6,10.20.0.1 # to use this server as the nameserver, edit /etc/resolv.conf: nameserver ::1 nameserver 127.0.0.1 # to set hostnames for static IPs, edit /etc/hosts: 127.0.0.1 localhost 10.20.0.1 perimeter 10.20.0.80 my-laptop
Here’s an example of a similar setup in a 10″ rack used by Grai for a long-term storage solution based on Ebenstahl:

Thanks for reading.

 Zwölf is an
Zwölf is an 
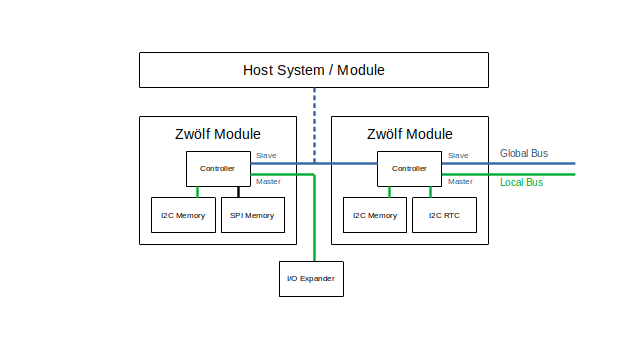
 Deep thinking often requires writing. The writing down of thoughts can be affected by perceived privacy. Thus, the erosion of perceived privacy may reduce the capacity for deep thought.
Deep thinking often requires writing. The writing down of thoughts can be affected by perceived privacy. Thus, the erosion of perceived privacy may reduce the capacity for deep thought.